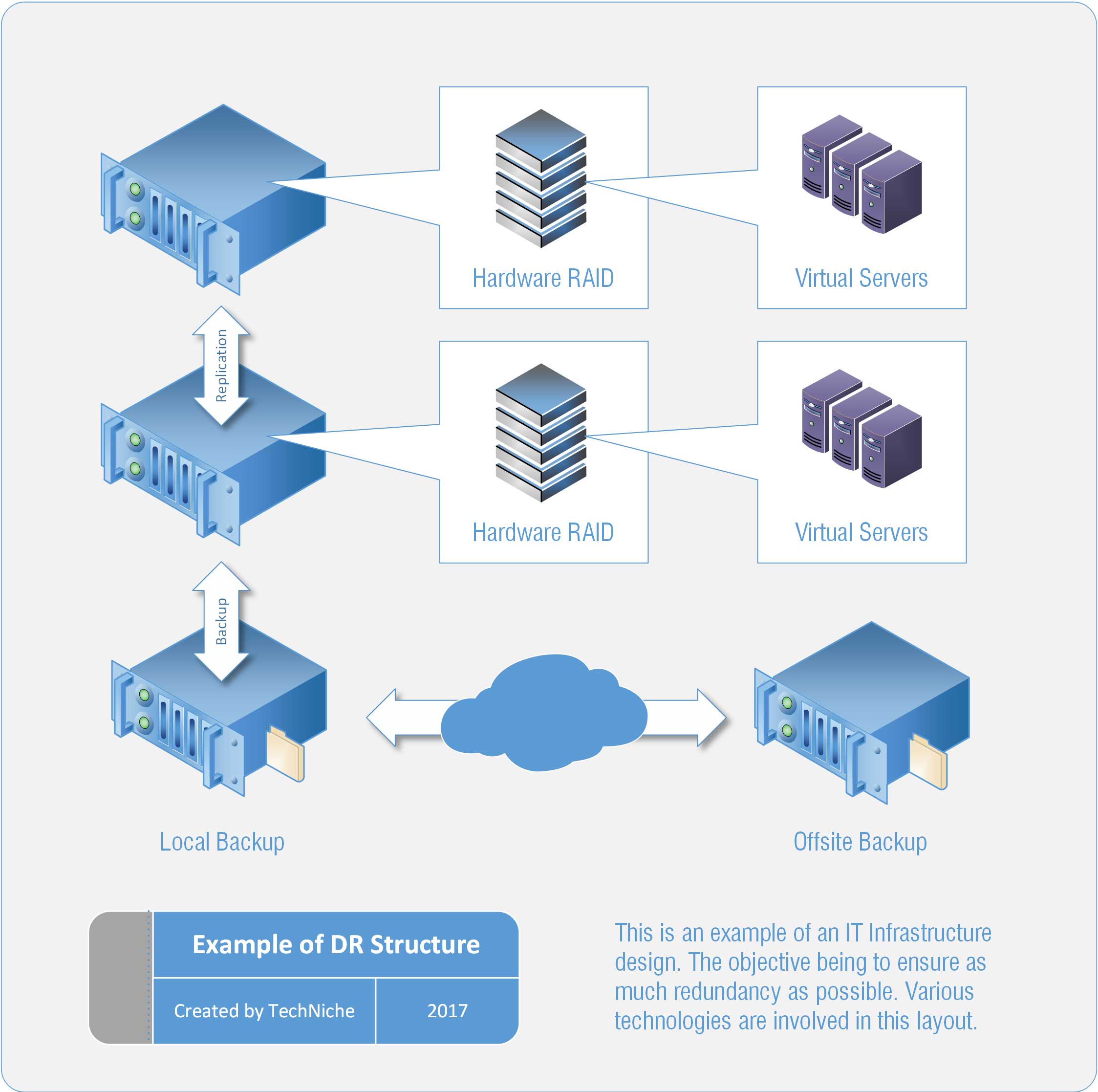
Sooner or later every business loses data. The value of that data cannot merely be measured in lost productivity while employees wait for systems to rebuild. Reputational damage, loss of income and production and possibly legal exposure could make the cost of disaster considerably worse.
While losing data can't be prevented, what impact that has on your business is entirely in your control. Our disaster recovery services focus on various preventative policies, procedures and systems. These allow a business to recover vital data once such has been lost due to natural or intentional causes. These are deployed before disaster strikes.
We offer the following disaster recovery services:
Area of focus |
Level of Automation |
|
1. |
Server fault tolerance |
Automated |
2. |
Onsite server backup |
Automated |
3. |
Onsite workstation backups |
Automated |
4. |
Replicated virtual machines |
Automated |
5. |
Offsite backup and replication |
Automated |
6. |
Testing of recovery procedures and/or backups |
Manual |
The combination of these efforts prevents the following risks:
Class of risk |
Protection required |
|
1. |
Accidental deletion (user error) |
Multiple backups |
2. |
Virus based deletion |
AV & Multiple backups |
3. |
Ransomware Virus |
AV & Multiple backups |
4. |
Hacking (human intentional actions) |
Security & Offsite backups |
5. |
Hardware failure (natural or intentional) |
Fault Tolerance and Backups |
This is addressed on the workstation and the server level.
In all cases we encourage as much automation and redundancy as possible. All systems are configured with a notifications and reporting framework in place. When the primary or backup systems encounter any failures we are informed and can start recovery right away.
A good DR plan is inextricably linked with the planning and implementation of your IT infrastructure. To this end, we plan each clients' systems in accordance with their needs and budgets. Not every client needs a system that will withstand an annual IT audit. Nor do all clients need to comply with a King III or Sarbanes Oxley compliance standard. Once the planning is done, systems are deployed and monitored. We carefully ensure that systems are documented, checked and monitored so that they behave predictably and within specifications. Finally, we test the DR to ensure that it delivers as needed. At this point important gaps are identified and unknowns are addressed. With this approach one can sleep peacefully knowing that one has a reasonable safety net for whatever may be just around the corner.